Hiob86,
October 9, 2019 to Jan 12, 2022 is 826 days (not including Jan 12th).
https://www.timeanddate.com/date/durationresult.html?m1=10&d1=09&y1=2019&m2=01&d2=12&y2=2022
This exceeds the 825 day requirement. If you'd just issue a shorter certificate (365 days for example) and it still had the problem, we can move on past the date issue. As is, it seems like that is at least one of your problems.
You are correct that when the validity period is your only issue, you do get a different error. I issued a test certificate exactly like the one that fixed my issue, but with a 10 year validity period, and it got the error "certificate is not standards compliant".

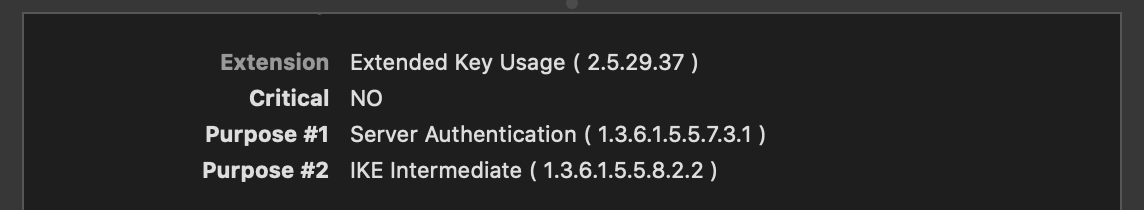
When I was comparing my internal certificates that had the issue and those that didn't, I did notice that Purpose #2 (see screenshot below) was missing on my broken certificate. That certificate was issued in 2015, so I assume my CA software updated the required minimal fields for TLS server certificates because the field is present on any certs I issue today. In terms of the article I shared and the listed requirements, I think IKE Intermediate under Extended Key Usage is the "TLS server certificates must contain an ExtendedKeyUsage (EKU) extension containing the id-kp-serverAuth OID" requirement Apple mentioned.
But in the end, our problem is that the error message "certificate name does match input" does not reflect the actual problem with the certificate. I believe this is because when failing the new requirements, in code the trusted host name list is empty and null doesn't match our input. Kind of an error priority issue when you have (to the best of my knowledge) code that only surfaces a single error message (the most critical) in the Show Certificate screen of Safari.