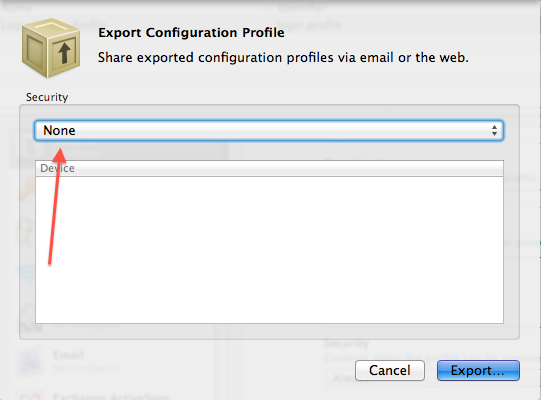
Nick, I received that error when when I signed the security profile during export. You need to make sure that you set security to "None" when you export. If you sign the profile you cannot make edits using a text editor because it breaks the signature (that's the whole reason why you would normally sign export files).
Here's some sample code that works for me.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>EAPClientConfiguration</key>
<dict>
<key>AcceptEAPTypes</key>
<array>
<integer>25</integer>
</array>
<key>EAPFASTProvisionPAC</key>
<false/>
<key>EAPFASTProvisionPACAnonymously</key>
<false/>
<key>EAPFASTUsePAC</key>
<false/>
<key>TLSAllowTrustExceptions</key>
<true/>
<key>UserName</key>
<string>XUSERNAME</string>
<key>UserPassword</key>
<string>XPASSWORD</string>
</dict>
<key>EncryptionType</key>
<string>WPA</string>
<key>HIDDEN_NETWORK</key>
<false/>
<key>PayloadDescription</key>
<string>Configures wireless connectivity settings.</string>
<key>PayloadDisplayName</key>
<string>Wi-Fi (TESTSSID)</string>
<key>PayloadIdentifier</key>
<string>login.profile.test.</string>
<key>PayloadOrganization</key>
<string>Organization Name.</string>
<key>PayloadType</key>
<string>com.apple.wifi.managed</string>
<key>PayloadUUID</key>
<string>34C68614-D32F-4BB4-875C-4B7341E63278</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>SSID_STR</key>
<string>XTESTSSID</string>
<key>SetupModes</key>
<array>
<string>System</string>
</array>
</dict>
</array>
<key>PayloadDescription</key>
<string>Profile description.</string>
<key>PayloadDisplayName</key>
<string>Test System 802.1X Profile</string>
<key>PayloadIdentifier</key>
<string>login.profile.test</string>
<key>PayloadOrganization</key>
<string>Organization Name.</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>1AFDCE61-788E-44DD-A487-68C33D18324E</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>