Hi vitaly_s,
Here is my edited mobileconfig file (I've removed personal information, but haven't touched the structure).
I've noticed that I did loose much time on the setup of my Active Directory objects. In fact, the way our RADIUS is set up, it checks both the computer and the user in AD and verifies if they are members of a VLAN group. If so, then after 802.1X authentication, they are assigned the computer's VLAN. (Your rules might be different though...). So, if you have similar rules, DON'T forget to assign these VLAN groups or else it won't work.
Since the big part of the configuration is the Network Payload part, I've attached the screenshot of my setup in Profile Manager.
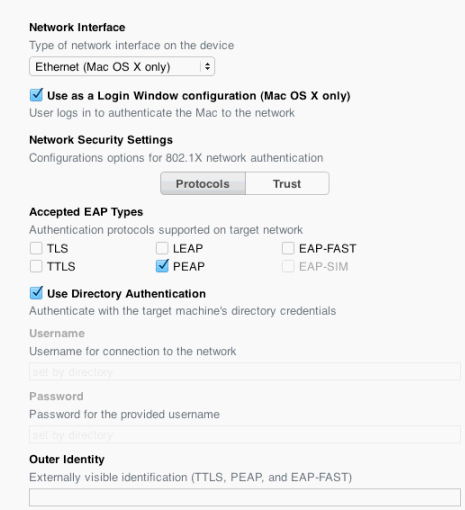
Here goes the XML! Enjoy!
---
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple Computer//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadContent</key>
<data>[MY CERTIFICATE DATA]
</data>
<key>PayloadDisplayName</key>
<string>svr21.toto.com</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>com.apple.mdm.minimac0001.toto.com.bd38dfc0-e08d-012e-0b99.alacarte.cer tificate.926B165C-5A45-48CB-8DD6</string>
<key>PayloadType</key>
<string>com.apple.security.root</string>
<key>PayloadUUID</key>
<string>926B165C-5A45-48CB-8DD6</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
<dict>
<key>PayloadContent</key>
<data>[MY CERTIFICATE DATA]
</data>
<key>PayloadDisplayName</key>
<string>svr26.toto.com</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>com.apple.mdm.minimac0001.toto.com.bd38dfc0-e08d-012e-0b99.alacarte.cer tificate.4DE7CCB5-60DD-4B6A-93F3</string>
<key>PayloadType</key>
<string>com.apple.security.root</string>
<key>PayloadUUID</key>
<string>4DE7CCB5-60DD-4B6A-93F3</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
<dict>
<key>AuthenticationMethod</key>
<string>directory</string>
<key>AutoJoin</key>
<true/>
<key>EAPClientConfiguration</key>
<dict>
<key>AcceptEAPTypes</key>
<array>
<integer>25</integer>
</array>
<key>EAPFASTProvisionPAC</key>
<false/>
<key>EAPFASTProvisionPACAnonymously</key>
<false/>
<key>EAPFASTUsePAC</key>
<false/>
<key>OneTimeUserPassword</key>
<false/>
<key>OuterIdentity</key>
<string></string>
<key>PayloadCertificateAnchorUUID</key>
<array>
<string>926B165C-5A45-48CB-8DD6</string>
<string>4DE7CCB5-60DD-4B6A-93F3</string>
</array>
<key>SystemModeCredentialsSource</key>
<string>ActiveDirectory</string>
<key>TTLSInnerAuthentication</key>
<string>MSCHAPv2</string>
<key>UserName</key>
<string></string>
<key>UserPassword</key>
<string></string>
<key>tlsTrustedServerNames</key>
<array/>
</dict>
<key>EncryptionType</key>
<string>Any</string>
<key>HIDDEN_NETWORK</key>
<false/>
<key>Interface</key>
<string>FirstActiveEthernet</string>
<key>PayloadDisplayName</key>
<string>Wired 802.1X</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>com.apple.mdm.minimac0001.toto.com.bd38dfc0-e08d-012e-0b99.alacarte.int erfaces.184dbc20-e158-012e-0b9f</string>
<key>PayloadType</key>
<string>com.apple.firstactiveethernet.managed</string>
<key>PayloadUUID</key>
<string>184dbc20-e158-012e-0b9f</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>ProxyType</key>
<string>None</string>
<key>SetupModes</key>
<array>
<string>System</string>
<string>Loginwindow</string>
</array>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>Settings for 802.1X</string>
<key>PayloadIdentifier</key>
<string>com.apple.mdm.minimac0001.toto.com.bd38dfc0-e08d-012e-0b99.alacarte</st ring>
<key>PayloadOrganization</key>
<string>802.1X Profile</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>bd38dfc0-e08d-012e-0b99</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>