Thank for your response! Here is the log:
alias_maps = hash:/etc/aliases
biff = no
command_directory = /usr/sbin
config_directory = /etc/postfix
content_filter =
daemon_directory = /usr/libexec/postfix
debug_peer_level = 2
enable_server_options = yes
header_checks =
html_directory = /usr/share/doc/postfix/html
inet_interfaces = localhost
local_recipient_maps =
mail_owner = _postfix
mailbox_size_limit = 0
mailbox_transport = dovecot
mailq_path = /usr/bin/mailq
manpage_directory = /usr/share/man
message_size_limit = 0
mydestination = $myhostname, localhost.$mydomain, localhost
mydomain = example.com
mydomain_fallback = localhost
myhostname = example.com
mynetworks = 127.0.0.0/8
newaliases_path = /usr/bin/newaliases
owner_request_special = no
queue_directory = /private/var/spool/postfix
readme_directory = /usr/share/doc/postfix
recipient_delimiter = +
relayhost =
sample_directory = /usr/share/doc/postfix/examples
sendmail_path = /usr/sbin/sendmail
setgid_group = _postdrop
smtpd_client_restrictions = permit_mynetworks permit_sasl_authenticated permit
smtpd_enforce_tls = no
smtpd_helo_required = no
smtpd_helo_restrictions =
smtpd_pw_server_security_options = login,plain,gssapi,cram-md5
smtpd_recipient_restrictions = permit_sasl_authenticated permit_mynetworks reject_unauth_destination permit
smtpd_sasl_auth_enable = yes
smtpd_tls_CAfile = /etc/certificates/example.com.E8236D8446AABAAEF98B22D64C6A69F4AA8E4E79.chain.pe m
smtpd_tls_cert_file = /etc/certificates/example.com.E8236D8446AABAAEF98B22D64C6A69F4AA8E4E79.cert.pem
smtpd_tls_exclude_ciphers = SSLv2, aNULL, ADH, eNULL
smtpd_tls_key_file = /etc/certificates/example.com.E8236D8446AABAAEF98B22D64C6A69F4AA8E4E79.key.pem
smtpd_tls_loglevel = 0
smtpd_use_pw_server = yes
smtpd_use_tls = yes
tls_random_source = dev:/dev/urandom
unknown_local_recipient_reject_code = 550
virtual_alias_domains = $virtual_alias_maps
virtual_alias_maps = $virtual_maps
Unfortunately didn't find anything useful in Console.app 😟 just a lot of garbage
We have a publick/static IP.
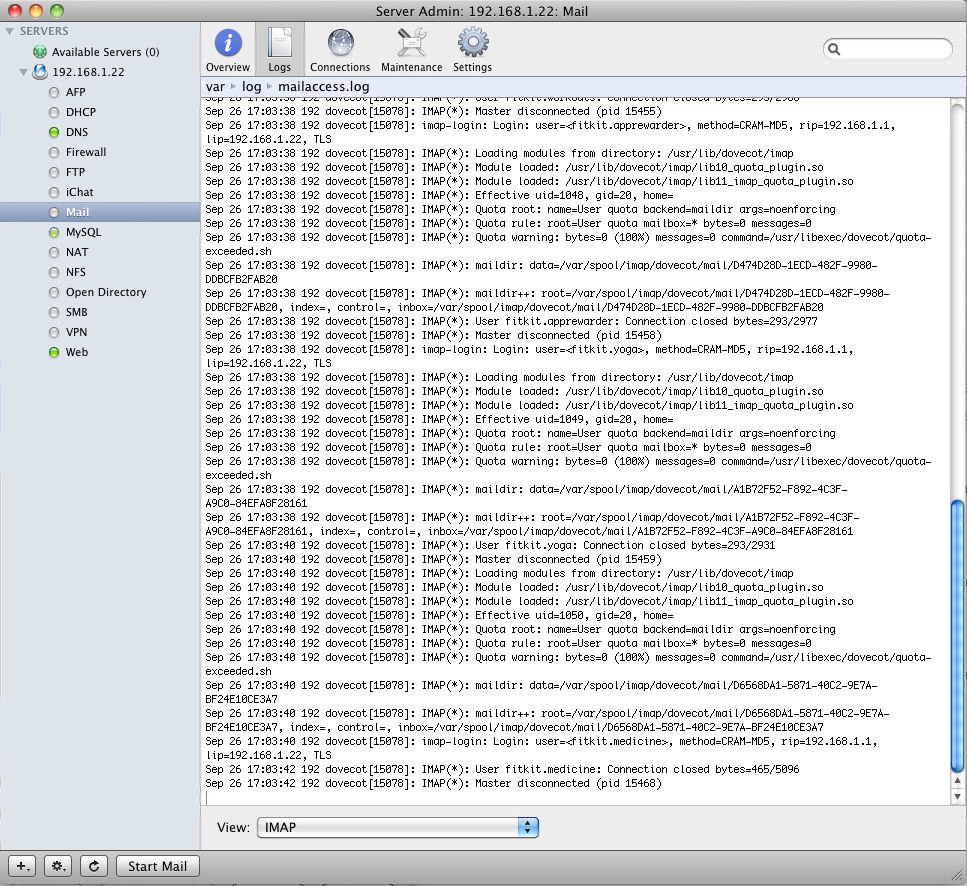
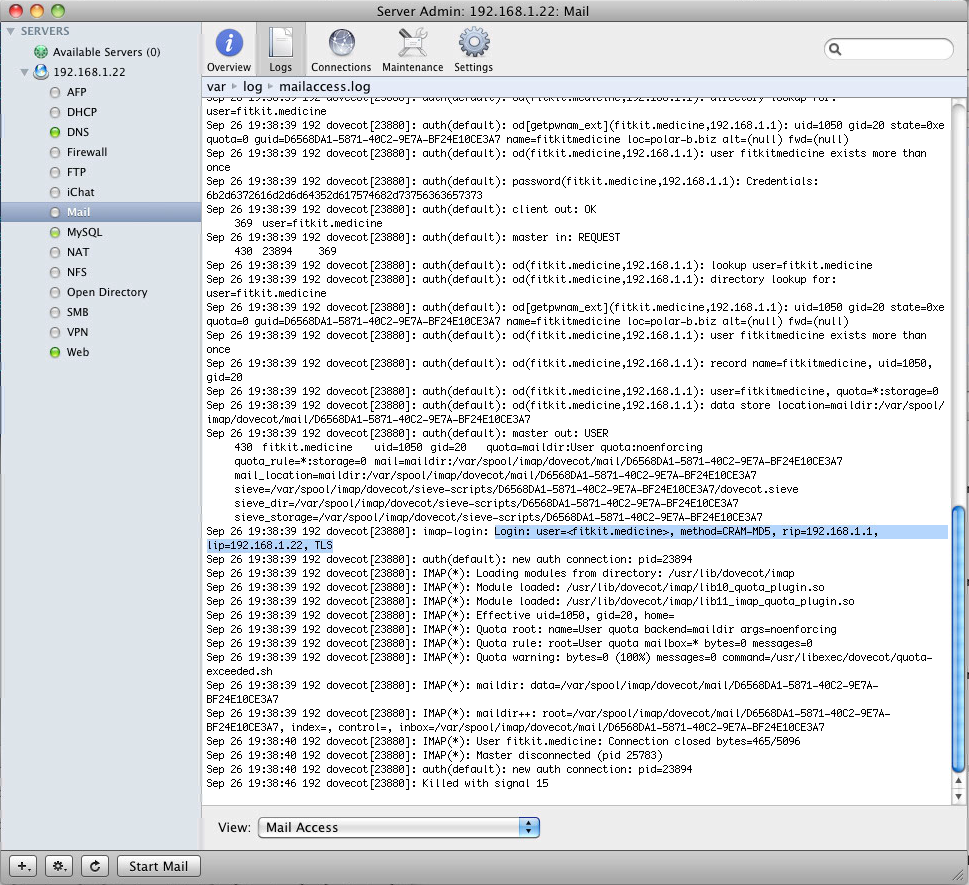
Also, here is logs from Admin panel (IMAP log, SMTP log and ACCESS log):