My phone has been remotely hacked and has been rooted. How do I find them?
copy of wakeupbackup? In analytics and analysis.. need help..
iPhone XR, iOS 16
copy of wakeupbackup? In analytics and analysis.. need help..
iPhone XR, iOS 16
Your device has not been hacked. Your log files are simply that, diagnostic information designed to assist an engineer in assessing information about a device.
Hello Nichole_McElroy,
Welcome to Apple Support Communities!
We want to help ensure your account and device are secure like you expect.
We see you viewed the Apple Support page for About Lockdown Mode - Apple Support
This Apple Support page some signs your Apple ID might be compromised:
"Signs your Apple ID has been compromised
Your Apple ID might be compromised if you receive an account notification from Apple for a change you didn't make, or if you notice account details or changes you don’t recognize. For example:
If you received an email, text message, or phone call that you're not sure is valid or you think might be phishing, here are some tips to help determine its legitimacy."
This Apple Support page has the full details and additional steps to take if needed to secure your account: If you think your Apple ID has been compromised - Apple Support
To keep your iPhone protected, make sure you have the latest updates installed: Update your iPhone, iPad, or iPod touch - Apple Support
"Update your iPhone or iPad wirelessly
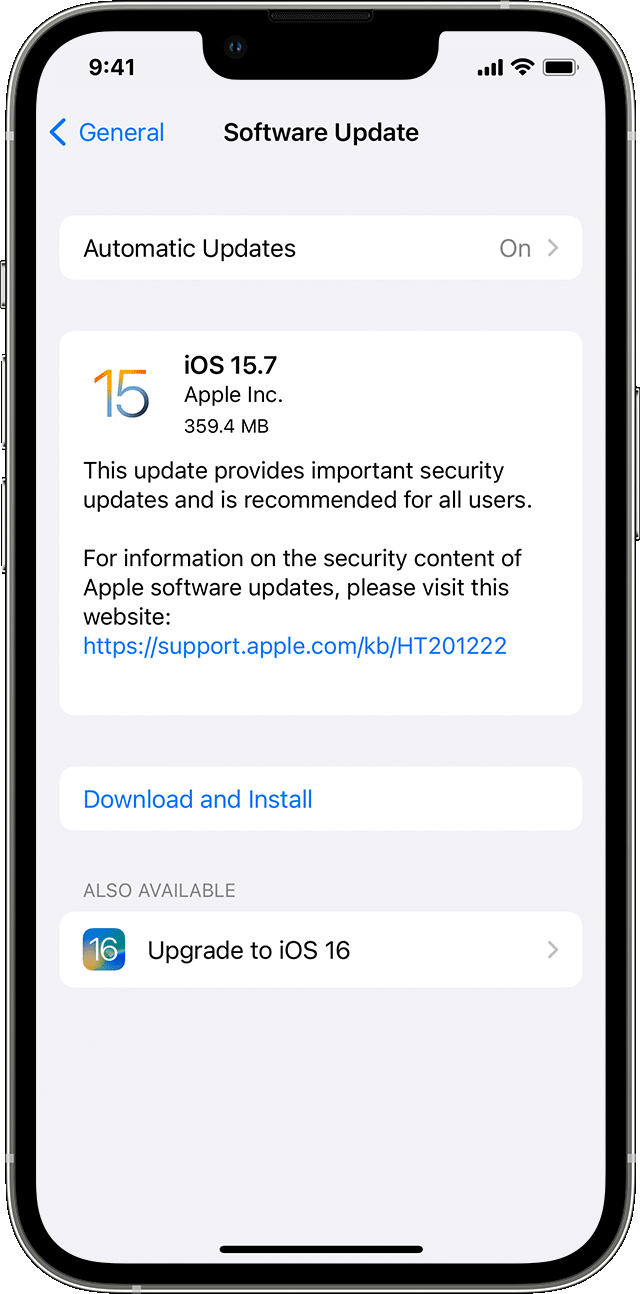
5. Tap Install Now. If you see Download and Install instead, tap it to download the update, enter your passcode, then tap Install Now. If you don't know your passcode, learn what to do."
If you continue to have issues with the security of your device or account, please reach out to an Apple Support Advisor for further assistance: Get Support
We hope this helps to ensure your account and device are protected.
Cheers!
How come nobody will actually answer this with cognitive words and descriptions? Just pasting info that is already findable in support pages IS NOT NOT NOT NOT an answer! PLEASE somebody do better than this EVEN IF maybe it’s “normal” there is no reason to shame someone for posting it and asking. You hackers never want to actually divulge info about what someone ACTUALLY posts! No descriptions no explanations of the lines of info … NOTHING. Somebody with code and computer language knowledge needs to actually give answers. Please. And if it’s normal, please explain WHY IT IS NORMAL, explain what EACH line means THANK YOU
My phone has been remotely hacked and has been rooted. How do I find them?