There are several reasons why you may see this behaviour.
Some embedded image content must be directly downloaded, by the Mail client, from its source. If this content is no longer available - or is blocked (as it may potentially contain malware, trackers or other threat) by your Mail, browser, DNS filtering or device settings - you may just see a “?” as you have described.
Apple’s default Mail settings also now initially block download of embedded content - whereas iPadOS14 and earlier this behaviour had to be configured if required. This security measure is intended to inhibit loading of potentially unsafe content - until such time as the recipient has had opportunity to review the email and determine whether or not the received email is from a trusted or expected source. Where images and other content have not been dowloaded, you may see a message at the top of the received email:

Whilst not recommended, should you wish to change this protective behaviour and automatically download all content, a simple change can be made in your device settings:
Settings > Mail > Privacy Protection > Block All Remote Content - set to OFF
This screenshot shows the relevant setting in its more secure state:
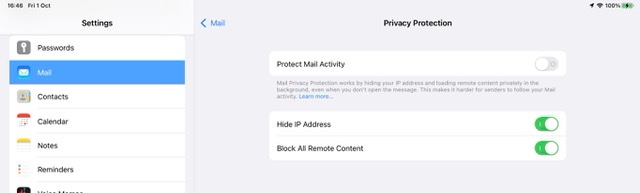
If settings are left is their more secure state, embedded content can be simply loaded if appropriate using the Load All Iimages button:
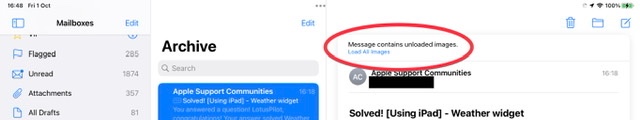
it is perhaps worthwhile to understand the reasoning for the default behaviour - whereby embedded images are not initially loaded…
By delaying loading of images until the body text is verified by the recipient, potentially malicious content and trackers are not loaded before the recipient has had opportunity to verify that the email is from an expected source or sender - or, for unsolicited email, taken the positive decision to download all content. Most legitimate email has adequate “body” to establish whether of not the email is (a) legitimate and (b) of interest to the sender.
If instead all content is loaded by default, malicious content is given opportunity to run malicious code or attempt a malware exploit. Similarly, images that contain (or are themselves) trackers will notify the actor that the email has been opened. At the very least, the sender of a broadcast phishing email is notified of a “live” mail account and recipient.
Additional supporting info can be found here:
If you see 'Unable to load remote content privately' at the top of an email - Apple Support