I've covered this previously here: Files & Folders not inheriting ACL pe… - Apple Community
The issue is that Apple broke the UI for proper permissions application long ago. You must use the command line to properly set file and directory inherit on your parent folder.
Let's create a simple example. You have a folder in /Users/Shared called Data. You want to share the Data folder and apply permissions to allow a group of users to have equal access to all children and descendants within the folder. Ideally, you will be creating a group and adding a group to the permissions table. For example, when initially adding a folder to Sharing, you will see three permissions entries. These are known as the POSIX permissions. From the top down, it is the Owner, Group, and Everyone. Here is an example:
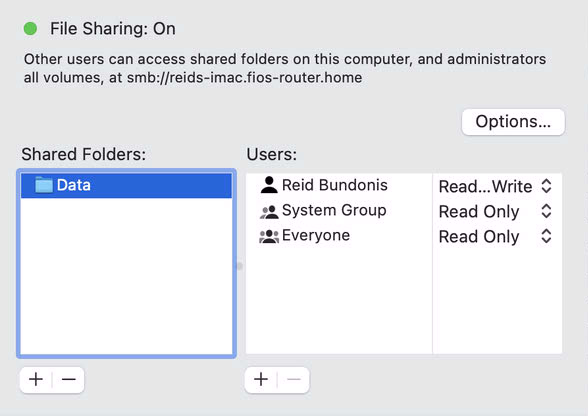
Using the Terminal command to list the contents and the permissions of the /Users/Shared folder:
ls -lae /Users/Shared
we see the same POSIX permissions represented by the drwxr-xr-x.
drwxr-xr-x 2 rbundonis wheel 64 Aug 10 07:35 Data
This means:
• the item we are looking at is a directory (d)
• the Owner (rbundonis) has Read (r), Write (w), and Execute/Traverse (x) rights (the first set of rwx)
• the Group (wheel) has Read (r) and Execute/Traverse (x) rights (the second set of r-x)
• Everyone has Read (r) and Execute/Traverse (x) rights (the final set of r-x)
You now must add an ACE (access control entry) to build your ACL. In this example, I've used the group called Designers. If you are not using Server.app, the group can be created in System Preferences > Users & Groups. Create the group first, then add users to it. Once your group(s) is/are defined, go to Sharing and add an entry to the permissions table, setting your group as the ACE. Define the permission as Read and Write.
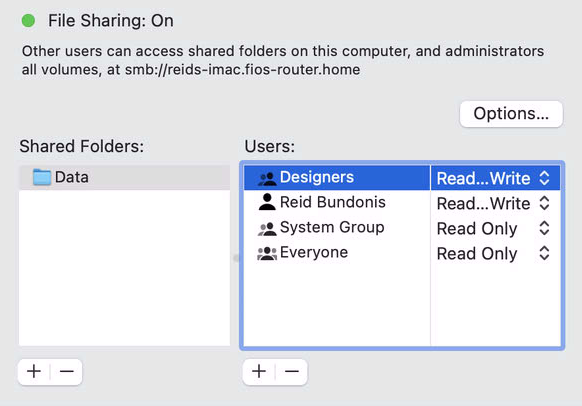
One would think this is all that is needed... Think again. This is where Apple's UI tools have been broken for years. To see what the action above did, run this command from Terminal once again:
ls -lae /Users/Shared
You will now see this result:
drwxr-xr-x+ 2 rbundonis wheel 64 Aug 10 07:35 Data
0: group:Designers allow list,add_file,search,add_subdirectory,delete_child,readattr,writeattr,readextattr,writeextattr,readsecurity
Note the POSIX permissions have not changed. But you now have an ACE that creates your ACL. Examine the entry. Note that the is no file or directory inheritance in your list of rights. You must add that in. To do that, use this command (replace paths and folder names to match your environment):
chmod =a# 0 "Designers allow list,add_file,search,add_subdirectory,delete_child,readattr,writeattr,readextattr,writeextattr,readsecurity,file_inherit,directory_inherit" /Users/Shared/Data
This command sets the ACE # 0 to allow the Designers group to list, add_file, search, .... file_inherit, directory_inherit on the folder /Users/Shared/Data.
Run this command once more to compare the ACE created by System Preferences to the one you modified with the chmod command:
ls -lae /Users/Shared
Now you have the proper ACL set. Quit System Preferences. Launch System Preferences and select Sharing. (the quit and launch are needed as you made changes outside of System Preferences. By quitting and launching, System Preferences rereads the state of the permissions on disk). Right-click on the Data folder and choose Apple Permissions to Enclosed Items.

While the propagation of permissions is happening, the permissions entries will turn gray. Wait until they turn black again. This means the inheritance propagation is complete. Please note, large data sets equal long propagation times. Wait for it.
If you have any clients with the Share mounted, unmount the share. Now mount the share to allow the client to read the new permissions table.
Permissions inheritance is now on and all users will have proper rights to all files and folders.
Hope this is helpful. Don't expect a fix from Apple any time soon. This has been broken since Mojave. Remember, Server is dead.
Reid